The Merriam-Webster Dictionary defines “cybersecurity” as “measures taken to protect a computer or computer system, as on the Internet, against unauthorized access or attack.”
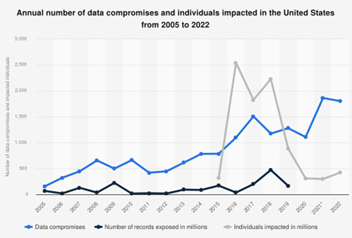
During the past two decades, cybersecurity has become a popular subject. Whenever news about hacking hits the headlines, the general public usually feels concerned and mostly confused while cybersecurity professionals are busy patching security holes. We keep hearing about more incidents and breaches on increasing scales, with more damages, and at a higher frequency. Cybersecurity seems to not be getting better (see Figure 1). It might be helpful to step back, look at the big picture, and find where we are before we get lost.
The Beginning
The modern computer was created in 1945 for processing and storing data. Because human beings inevitably make mistakes in designing and implementing hardware and software, security vulnerabilities or flaws have existed since the computer was born. Consequently, cybercrimes taking advantage of those vulnerabilities are as old as the computer itself. When computers were standalone, the security issues were relatively under control. Passwords were widely used to secure data stored in computers in the early days. In 1949, John von Neumann introduced the possibility of creating a program that could reproduce itself. He established the theoretical foundation of malware, a special software species whose sole purpose is to disrupt and destroy, such as computer viruses and worms. Ironically, von Neumann was also the inventor of modern computer architecture.
Phone “phreaking” was the earliest hacking against electronic devices, popular in the 1950s. Hackers used various means to manipulate the public telephone system for placing free long-distance calls. The inception of modern cyber-attacks (and the need for cybersecurity) occurred in the 1970s when the ARPANET, the early form of the Internet, started to connect computers with networking devices and turn global data communication into reality. Bob Thomas, an ARPANET developer and the first cyber offender in cyberspace, created the first computer worm called “the Creeper.” This program was designed to print harmless lines on victims’ screens while migrating from host to host on the Internet. Ray Tomlinson, an ARPANET researcher and also the first cyber defender, developed a program called “the Reaper” to hunt down and eliminate the annoying “Creeper” worms. This was a battle marking the beginning of the Cyberwar, which we are still fighting today, between the offenders and the defenders in cyberspace. Before long, more malware, including worms, trojan horses, and viruses, emerged, and countermeasures, such as antivirus software, were developed to fight against them. In the 1980s, with increasing cyber espionage threats throughout the Cold War, the term “cybersecurity” was first coined. However, this term was irrelevant to ordinary people who were not computer users then.
Starting circa the late 1990s, the increasing popularization of personal computers with the significant expansion of the global World Wide Web attracted everyone to cyberspace from all over the world. However, the underlining technology of the Internet was not designed with security in mind. The inevitable vulnerabilities in computer systems combined with the faulty design of Internet technology created a perfect storm. Threat actors, or cybercriminals, found a new Wild West to disrupt, steal, eavesdrop, and blackmail. Suddenly, using a computer was not safe. Computer hardware and software vendors realized they had too many security holes to patch. Researchers were busy revising existing technologies while proposing new technologies to fight against cyber-attacks.
In the recent decade, computers, mobile devices, and the Internet have become inseparable from everybody’s life. The cybersecurity industry has witnessed ubiquitous disruptions and damages caused by cyber offenders, ranging from nuisances to life-threatening disturbances. Numerous big-name companies and organizations, such as SONY, Target, Yahoo, Home Depot, Snapchat, Equifax, and DNC, to name a few, have fallen under cyber-attacks, leading to massive exposure of customers’ Personal Identification Information, substantial financial losses, as well as compromises of national security and political system integrity. More attacks have targeted IoT, embedded systems, and industrial SCADA systems, causing physical disruptions and damage. The war is getting ugly.
The Present
During 2022, the cyber security industry faced a highly volatile threat landscape impacted by COVID, macroeconomic turbulence, and the Russian war against Ukraine. High-profile data breaches leveraged supply chain vulnerabilities to target critical infrastructure. Many cybersecurity professionals reported increased workload, especially in financial services, aerospace, government, and military fields (2022 ISC2 Cybersecurity Workforce Study Report).
The Verizon 2022 Data Breach Investigation Report shows the human (error) element continued to be the weakest link in cybersecurity, involved in 82% of the breaches. The top two motives for breaches in 2022 were financial and espionage, around 90% and 6%, respectively. The top two breach vectors were web servers and email systems, which are the main surfaces exposed to cyber offenders. The top two breach actions were malware (combined with social engineering) and remote hacking against web applications. The main hacking techniques were stolen credentials stuffing, ransomware, phishing, pretexting, and system vulnerability exploitation. Notably, ransomware-oriented breaches continued to grow in 2022, about a 13% increase from the previous year. The supply chain issues, such as Log4J and SolarWinds, were responsible for 62% of the system intrusion incidents. Organized crime accounted for 79% of breaches, compared to 49% in 2018. A majority (70%) of the breaches were detected within days or less, an increase from less than 40% in 2017. However, more than 50% of the breaches were discovered through “Actor Disclosure,” which means either the hacker sent a ransomware note, announced the breach, or sold the data in the darknet; all are the worst case for victims.
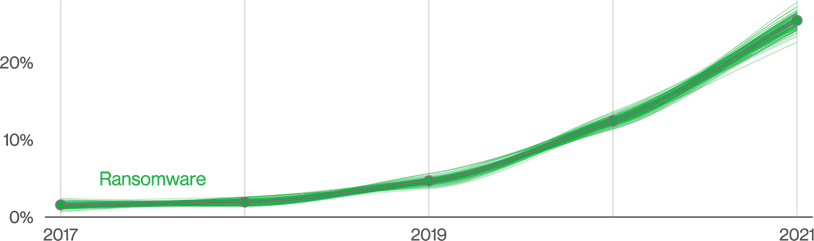
Hackers in ransomware attacks no longer care about what they can steal or destroy after compromising victims’ computer systems. Instead, they block the victims from accessing their vital data using encryption and ask for ransoms. Ransomware attacks have become an efficient way for hackers to monetize their unauthorized access to victims’ data with relatively low risks, dramatically changing the cybersecurity landscape. Hacking has become a business where anyone can hire hackers to provide “Hacking as a Service” (HaaS) or “Ransomware as a Service” (RaaS). Many trends in 2022 were mainly due to the recent rise of ransomware (see Figure 2).
In 2022, the world was still facing an increasing gap in the cybersecurity workforce. The ISC2 Workforce Report shows cybersecurity professionals are highly educated and well-trained, with 39% with a bachelor’s degree, 43% with a master’s degree, 5% with a doctorate, and 96% with at least one certification. The global cybersecurity workforce is estimated at 4.7 million, with an 11% growth over the previous year. The workforce gap, estimated at 3.4 million, has increased by 26% compared to the previous year. The gap grows twice as fast as the workforce! As a result, nearly 70% of organizations say they have a worker shortage. The demand for cybersecurity professionals will continue to overwhelm the supply as the threats in the cyber world become more motivated, sophisticated, and resourceful.
The New Challenges
Today, we have seen newer technologies become available to both cyber defenders and offenders, bringing new opportunities and posing new challenges to cybersecurity professionals simultaneously.
• AI and Intelligent Automation
Artificial Intelligence, namely machine learning techniques, has been employed broadly to support intelligent security operational functions, such as dynamic malware and intrusion detection. A survey shows 57% of cybersecurity professionals have used AI technology to automate aspects of the security job, and 26% plan to do so (ISC2 report). AI and automation may help cybersecurity professionals to focus on higher-level tasks and reduce the staffing shortage. However, like every software system, AI is vulnerable to cyberattacks, such as input data poisoning and manipulation. On the other hand, the attackers in the dark are more than happy to deploy various AI techniques to automate the attacks and gain an advantage. In the recent ChatGPT wave, hackers have used this new AI technology to help write malware and polish phishing emails. AI is a double-edged sword. Cybersecurity researchers must study how to secure an AI system and deploy “good” AI technology in cyber defense while bracing for attacks from a “bad” AI designed by an offender. AI and cybersecurity researchers should also start to look at the security of AI singularity, a concept first introduced by, again, John von Neumann to describe the future possibility where machine intelligence surpasses human intelligence. A machine with superintelligence might be the most dangerous hacker and threat to human society.
• Blockchain and IoT
Internet of Things with embedded systems is the new face of the Internet, ranging from mobile devices, medical devices, and “smart” home devices to connected vehicles, industrial sensors, controllers, and so on. They can adjust our room temperatures, operate our cars, and manage power grids, water towers, pipelines, and critical national infrastructure. However, the recent Palo Alto Networks Report stated that 98% of IoT device traffic was unencrypted and described IoT devices as easy targets for cyber attackers. Blockchain uses a non-traditional dispersed Public Key Infrastructure model and distributed ledger system to provide strong authentication, accounting, and non-repudiation for secure communication. Research has been conducted to deploy blockchain technology in securing IoT/embedded ecosystems.
Meanwhile, data privacy and scalability are the biggest challenges blockchain technology faces. Cryptocurrencies, which use blockchain technology, have also become a major cybercrime target. Chainalysis, a blockchain research company, estimated that around $2 billion worth of cryptocurrency was stolen in 2022. Notably, when an attack against a blockchain ecosystem occurs, its decentralized structure is slower to react compared to a traditional centralized system. More research is needed on blockchain applications and their security.
• Quantum Computing and Cryptography
Contemporary Cryptography is the most crucial pillar of cybersecurity. The fundamental design of cryptography is the “computational infeasibility” feature in many cryptographic algorithms. In theory, the feature ensures that it would be computationally impossible for anyone to guess or calculate the secret within a reasonable amount of time, even with the most powerful computer available. Quantum Computing, dubbed in the 1980s and still an infant, might shake or even destroy this fundamental design. Quantum computing uses quantum bits, refers as “qubits,” and leverages the “Quantum Entanglement” phenomenon to achieve true parallel processing and an exponential increase in computing power. When this technology matures and becomes widely available, it will bring a revolutionary change in computing and render existing cryptographic algorithms useless. Cybersecurity researchers must prepare to entirely revamp the cryptographic design and implementation for the cybersecurity industry.
The Future
The following observations in recent cyber incidents suggest that future cyber offenders might be more determined, better organized, and more “professional.” None of the factors will favor cyber defenders, and the combined effect will be devastating.
• More cyber-attacks are motivated by financial gains because ransomware attacks provide high profit with low risk to the criminals.
• The emergence of HaaS and RaaS has turned cyber-attacks into common, typical crimes, blurring the line between cyber and the physical world.
• Cyber-attacks are increasingly backed by nation-states and used as a precursor to military conflict and tactics of military operations.
• A world with increasing geopolitical conflicts continues to make attribution, remediation, and penalization of cyberattacks extremely difficult, if not impossible, especially for trans-border attacks.
The rise of ransomware is a good indication of the dramatic change in the cyber threats landscape. Nowadays, typical cyber offenders are no longer “script kiddies” or opportunists to cause a nuisance or make a political point. They are well-trained professionals working as a team and hired by criminal organizations or backed by nation-states, with more resources, patience, and determination. Given time and armed with the latest computing facilities and technology, these so-called Advanced Persistent Threats (APT) will always find a way in. The question is not if, but when. After all, the wave of cybercrimes will not subside, and the cat-and-mouse game in cyberspace will continue, just as the fight against crimes has lasted as long as human history and shows no sign of being won.
Cybersecurity Education
When the scale and volume of cyber threats are rampant, with new challenges continually emerging, the world is facing a significant cybersecurity worker shortage. We need more protectors, soldiers, and innovators to up the game. Education is undoubtedly the most critical and urgent task. A well-rounded education system should produce capable professionals and researchers to build this much-needed elite force. The US government has been working in this direction through the National Initiative for Cybersecurity Education (NICE), aiming to “enhance the overall cybersecurity posture of the United States by accelerating the availability of educational and training resources designed to improve the cyber behavior, skills, and knowledge of every segment of the population.”
The human element remains the most vital, yet the weakest, link in cybersecurity. Cyber awareness education programs have effectively reduced the “low-hanging fruits” of cyber-attacks in some public and private organizations. To further reinforce the human element, a more fundamental change in the education system, in terms of universal cybersecurity education, should be implemented to turn the whole population into the first line of defense against cybercrimes. In other words, the general public’s cybersecurity mindset and knowledge should be cultivated and honed through general education requirements, just as we already do for math and science knowledge and skills. As a metaphor, if cybercrimes are the flu, universal cybersecurity education is the flu shot to build a robust immune system for the public to fight against cybercrimes.
Cybersecurity Education at Eastern Michigan University
As one of the leading US institutions in cybersecurity education, Eastern Michigan University has been designated by the National Security Agency as a Center of Academic Excellence in Cyber Defense Education since 2005. The School of Information Security and Applied Computing (SISAC) in the GameAbove College of Engineering and Technology is committed to preparing prospective students with the knowledge and skill set necessary for future cyber security professionals to build, maintain and defend networks and computer systems in both government and industry against cyber attacks. SISAC offers a spectrum of cybersecurity education options, including bachelor’s, master’s, and PhD degrees and various certificates. The Bachelor of Science in Cybersecurity program has been accredited by the Accreditation Board for Engineering and Technology (ABET) since 2018.
Sign up today for a free Essential Membership to Automation Alley to keep your finger on the pulse of digital transformation in Michigan and beyond.
Dr. Che is a Professor and the Director of the School of Information Security and Applied Computing in the GameAbove College of Engineering and Technology at Eastern Michigan University. Before his academic career, he worked as a system and network engineer in the IT industry for approximately 20 years. Dr. Che received his BE in Electrical Engineering and ME in Computer Engineering from Zhejiang University, his MS in Software Engineering from Bowling Green State University, and his Ph.D. in Computer Science from Wayne State University. His main research interests are cybersecurity and computational intelligence. He is the author and co-author of multiple research publications and holds several IT and Cybersecurity professional certifications.




